BACKUP, RESTORE, AND PROTECT Audit and Employee Productivity
USER ACTIVITY MONITORING
Activity Monitoring, User Behavior Analytics, Productivity Optimization & Insider Threat Detection in a Single Platform
Protect Your Data
Most organizations have cybersecurity measures in place including antivirus, firewall, intrusion detection to protect infrastructure and IT assets. These tools are good at defending organizations from external threats.
However, they leave a security hole to users who already have access to an organization’s valuable assets and sensitive data. These users include employees, internal users, third party vendors, contractors and privileged administrators.
How To Monitor User Activity
User activity monitoring is the process of monitoring web activity of users. With a PC activity monitoring solution in place, businesses have the necessary means to keep an eye on their sensitive data.
With UAM, businesses can monitor web activity of users to identify and stop the misuse of company data and resources.
Teramind User Activity Monitoring Combines UAM, Behavior Analytics, and Productivity Tools
Teramind user activity monitoring goes beyond the basic employee monitoring and the computer activity tracker functionality. Teramind’s UAM adds intelligent behavior-based analysis to provide actionable insights.
User Activity Monitoring And Productivity Tracking
Teramind’s PC activity monitoring also measures employee productivity. This system keeps track of how employees and third-party vendors access company resources. The PC activity monitoring system will also conduct risk analysis and prevent unauthorized data exfiltration.
Session Recordings To Monitor Web Activity Of Users
Finally, in case of a data breach or security incident, Teramind provides comprehensive forensic data and session recordings. These sessions recordings can identify the employees and vendors who have triggered a rule violation. Teramind’s user activity monitoring software will also show the user’s activity footprint with pinpoint accuracy.

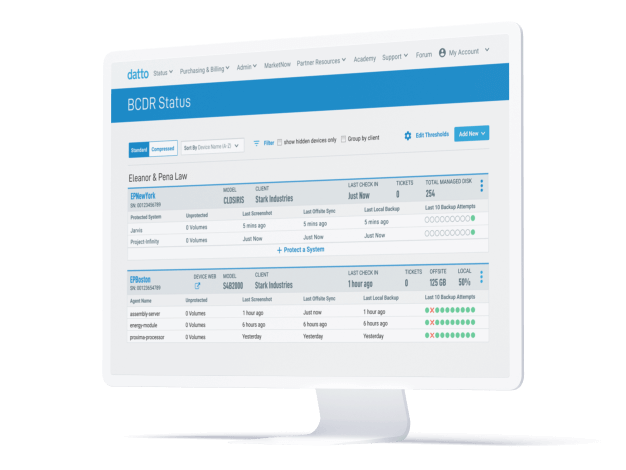
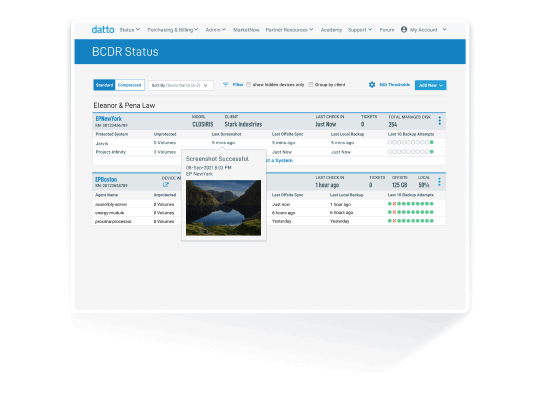
Protect Your Clients’ Azure Data
Workloads running in Azure are not automatically backed up. Ensure that you’re protected from single-cloud risk and downtime scenarios, such as ransomware and outages, with Datto Continuity for Microsoft Azure. Provide true business continuity for your clients with multi-cloud protection, hourly replication to the secure Datto Cloud, and no-cost egress.

Reliable Data Protection
Under Microsoft’s shared responsibility model, customers are responsible for keeping their data secure, protected and recoverable. Safeguarding your clients’ data is easy with Datto Continuity for Microsoft Azure.
Securely Backup and Recover Azure Workloads
Increase resilience while protecting against ransomware and other cybersecurity threats: The immutable Datto Cloud sets the standard for secure cloud infrastructure. Benefit from features like Cloud Deletion Defense™ and geographically distributed locations that guarantee data sovereignty.
Predictable Costs, Profitable Solution
Public cloud costs can be complex and limit your margins. Datto Continuity for Microsoft Azure eliminates the confusion of calculating your monthly cloud bill, with a flat-fee solution that covers all of your BCDR costs, including egress and virtualization.
Azure BCDR Purpose Built for MSP’s
Datto Continuity for Microsoft Azure was built exclusively for MSPs to easily manage client data protection at scale. You’ll be confident that your backups are complete, bootable, and easily recoverable, so you can minimize downtime for the businesses that depend on you.

Teramind Comes with Powerful User & Entity Behavior Analytics Capabilities
Teramind user activity monitoring features user and entity behavior analytics (UEBA) capabilities. These features identify and alert organizations to a wide range of anomalous behavior and potential threats.
Common areas threats come by are either a malicious, inadvertent or compromised employee, user or third-party entity. Using a PC activity monitoring software will identify and stop these threats quickly.
Teramind automatically creates a behavioral baseline taking into account a user’s activity. For example:
- Number of times a file is accessed
- Usage patterns
- Entity role
- Time of day
- Assigned project activites
Teramind monitors the web activity of users to find any anomaly or deviation from the normal baseline. When the PC activity monitoring system detects any abnormal behavior it will trigger real-time alerts and notifications.
Teramind’s Intelligent Policy & Rule Engine then combines this UEBA capability to proactively prevent insider threats. The system also provides the organization with a clear and complete picture of all activity, context and forensic evidence in a single solution.
Protect your business
Ensure assets are protected and employee actions are recorded.
File and Folder activity monitoring.
Monitor file activities in real-time
Audit all file activities, including creation, deletion, and modification. Receive insights on who made the changes, from where, and when.
Scrutinize failed access attempts
Track and manage unintended failed access attempts such as read, write, or delete before they escalate into critical security issues.
Enable rapid threat remediation
Shut down an infected device, disconnect a user session, or create your response strategy based on the security threat detected.