Secure your business with mobile device management solutions
Effective mobile device management solutions offer advanced capabilities to keep up with the ever-changing mobile landscape. IT and security leaders must manage laptops, desktops, smartphones, tablets, wearables and Internet of Things (IoT) devices. Having adequate visibility and management over a broad range of devices and operating systems may seem challenging but can be addressed when the right strategy and tools are in place.
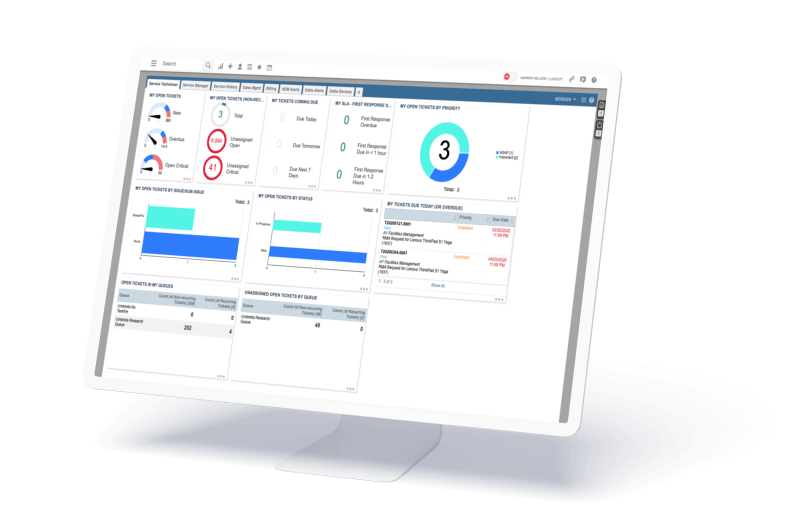

Visibility into your mobile environment
One MDM solution for any device with any OS
Manage the most popular device types and operating systems, including Android, iOS, macOS, Chrome OS and Windows 10 — all from a single mobile device management platform.
Seamless user on-boarding
Take advantage of easy, over-the-air (OTA) device enrollment for rapid deployment using the leading cloud MDM platform. With Apple Business Manager, streamline the device onboarding process for Apple devices, including the iPhone, iPad and Mac. Use Android zero-touch enrollment to deliver a secure, exceptional, out-of-the-box device setup experience to employees.
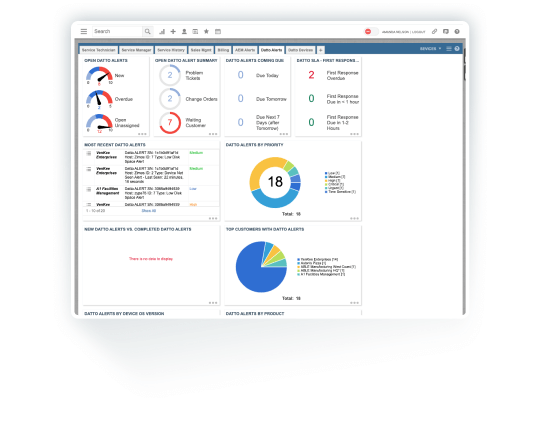
Mobile device management platform
Control and Protect your organization
Transform how IT secures smartphones, tablets, computers, wearables and the Internet of Things (IoT) without sacrificing a great user experience. Artificial intelligence (AI) and predictive analytics keep you alerted to potential endpoint threats and provide remediation to avoid security breaches and disruptions. IBM Security MaaS360 with Watson protects apps, content and data so you can rapidly scale your remote workforce and bring your own device (BYOD) initiatives.
Manage and Secure your workforce
Whether you are supporting iOS, Android, Windows, macOS or Chrome OS devices, IT administrators can quickly enroll and configure devices, manage identity and access, monitor usage, and secure your mobile infrastructure.
A MDM Platform Designed to Improve the
Management of your Business
Threat management
Enable enterprise-grade threat defense to detect threats and automate remediation across your users, devices, apps, data and network.
Containment
Protect corporate data and uphold compliance regulations with a secure container that enables productivity from devices.
Endpoint convergence
Frequently Asked Questions
In recent years, mobile devices have become ubiquitous for enterprise use. Businesses and their workforces rely on mobile devices like smartphones, tablets and laptops for an assortment of jobs. And as working remotely has become essential, mobile devices have become an integral part of most organizations—vital tools for productivity and efficiency.
But because enterprise mobile devices access critical business data, they can threaten security if hacked, stolen or lost. So, the importance of managing mobile devices has evolved. Such that IT and security leaders are tasked to provision, manage and secure mobile devices in their respective corporate environments
With a mature MDM platform, IT and security departments can manage all of a company’s devices no matter their type or operating system. It helps keep all devices secure while keeping the workforce flexible and productive.
A common question on the web is: Is mobile device management a piece of software? The short answer is yes and no. MDM is a solution that uses software as a component to provision mobile devices while protecting an organization’s assets like data. Organizations practice MDM by applying software, processes and security policies onto mobile devices and toward their use. Beyond managing device inventory and provisioning, MDM solutions protect the device’s applications, data, and content. In this sense, MDM and mobile security are similar. However, MDM is a device-centric approach, whereas mobile security and unified endpoint management have evolved to a user-centric stance.
In an MDM program, employees can receive a dedicated work device, like laptops or smartphones, or have a personal device remotely enrolled. Personal devices receive role-based access to enterprise data and email, a secure VPN, GPS tracking, password-protected applications, and other MDM software for optimal data security. MDM software can then monitor the behaviors and business-critical data on enrolled devices. And with more sophisticated MDM solutions, they can be analyzed by machine learning and AI. These tools ensure devices are kept safe from malware and other cyberthreats. For example, a firm might assign a laptop or smartphone to a staff member or consultant, pre-programmed with a data profile, VPN, and the other necessary software and applications. In this scenario, MDM offers the most control to the employer. With MDM tools, enterprises can track, monitor, troubleshoot and even wipe device data in the event of theft, loss or a detected breach.
So, what are mobile device management policies? MDM policies answer questions about how organizations will manage mobile devices and govern their use. To configure and publish their policies and processes, enterprises will ask questions, such as:
- Do devices need passcode protection?
- Should cameras be disabled by default?
- Is Wi-Fi connectivity important?
- What customization options will the device provide?
- Do certain devices need to be geo-fenced?
Device tracking
Each device enrolled with or issued by an enterprise can be configured to include GPS tracking and other programs. The programs allow an enterprise’s IT professionals to monitor, update and troubleshoot the device in real time. They can also detect and report high-risk or non-compliant devices and even remotely lock or wipe a device if lost or stolen.
Mobile management
IT departments procure, deploy, manage and support mobile devices for their workforce, like troubleshooting device functionality. They ensure each device comes with the needed operating systems and applications for their users, including applications for productivity, security and data protection, backup and restoration.
Application security
Application security can involve app wrapping, in which an IT administrator applies security or management features to an application. Then, it re-deploys the application as a containerized program. These security features can determine whether user authentication is required to open an app, whether data from the app can be copied, pasted or stored on the device, and whether the user can share a file.
Identity and access management (IAM)
Secure mobile management requires strong identity and access management (IAM). IAM allows an enterprise to manage user identities associated with a device. They can regulate each user’s access within an organization, using such features as single sign-on (SSO), multifactor authentication and role-based access.
Endpoint security
Endpoint security encompasses all devices that access a corporate network, including wearables, Internet of Things (IoT) sensors and non-traditional mobile devices. Endpoint security can include standard network security tools such as antivirus software and network access control and incident response, URL filtering and cloud security.